Top Notch Tips About How To Develop A Security Policy

When developing your cyber security policy consider the following steps.
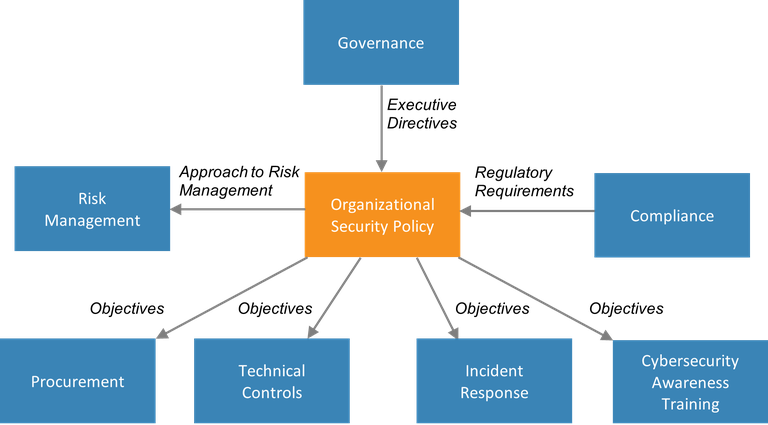
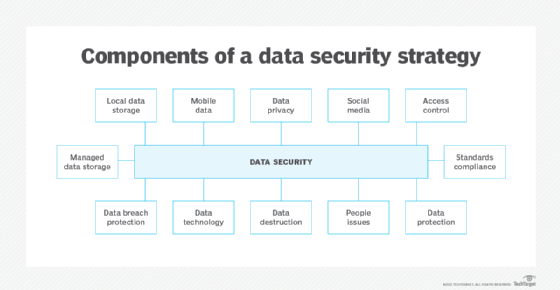
How to develop a security policy. An effective policy will use. The first step must be to gain a clear. Even by it standards, security is overrun by acronyms and jargon.
Start by creating broad policies. Identify your risks what are your risks from inappropriate use? Tips on how to develop a physical security policy 1.
Learn from others there are many types of. Fill out the name and details of the policy. To develop your security policy, you must clearly define your security objectives.
Developing a security policy from scratch can be an overwhelming task. In this case, it's security objectives. First, identify the buildings or places to be covered by the physical security policy.
Performing the following steps to develop a security policy talk with other members of your organization, such as security auditors, to better determine your security needs. How to develop security policy for your company 1. The first step in developing an information security policy is conducting a risk assessment to identify vulnerabilities and areas of concern.
Here are a few essential steps you need to take to create a successful cloud security policy. Handling and storage of sensitive material. How to create an effective security policy: